
This document describes configuration of Microsoft Active Directory as external identity store for administrative access to the Cisco ISE 3.2 management GUI and CLI.
Prerequisites
It is recommended that you have Cisco ISE 3.2 and Microsoft Active Directory knowledge and deployed in your network environment.
- Configuration of Cisco ISE Version 3.2
- Microsoft Active Directory
Integration of Microsoft Active Directory with Cisco ISE 3.2
Use this section to integrate Microsoft Active Directory as an External Identity store for administrative access with Cisco ISE 3.2
Configuration
Step 1: Join Cisco ISE 3.2 to Microsoft Active Directory
Login to Cisco ISE 3.2 using local administrator credentials.
- Navigate to -> Administration -> Identity Management -> External Identity Sources.
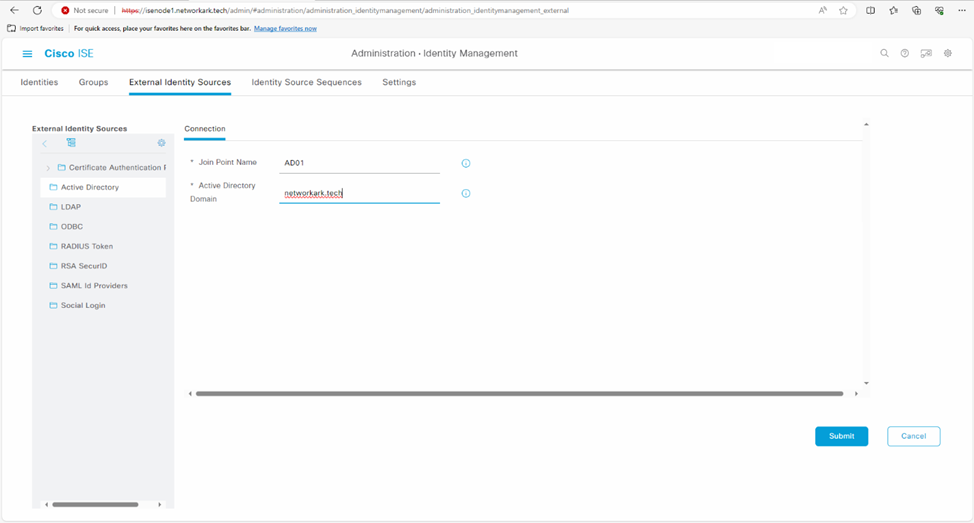
- Click on + Add button -> Add a new join point name and domain name -> Submit.
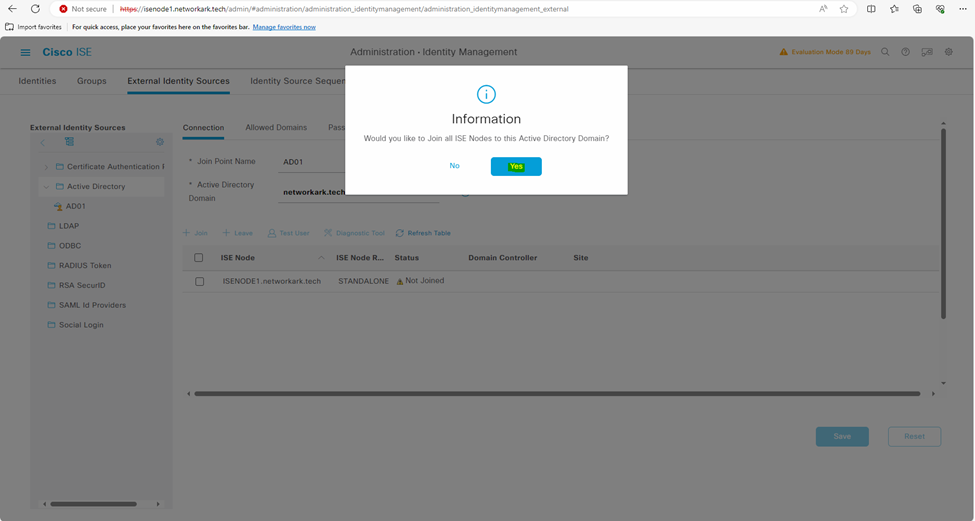
- Confirm Information window – > Yes.
- Enter Active Directory administrator account credentials to join Cisco ISE 3.2 to Microsoft Active Directory environment. You may optionally specify an Organization Unit
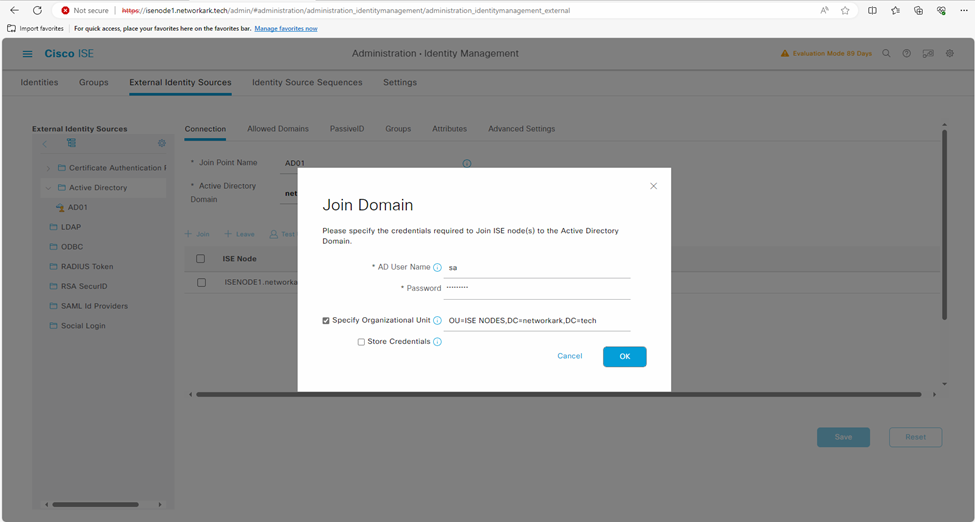
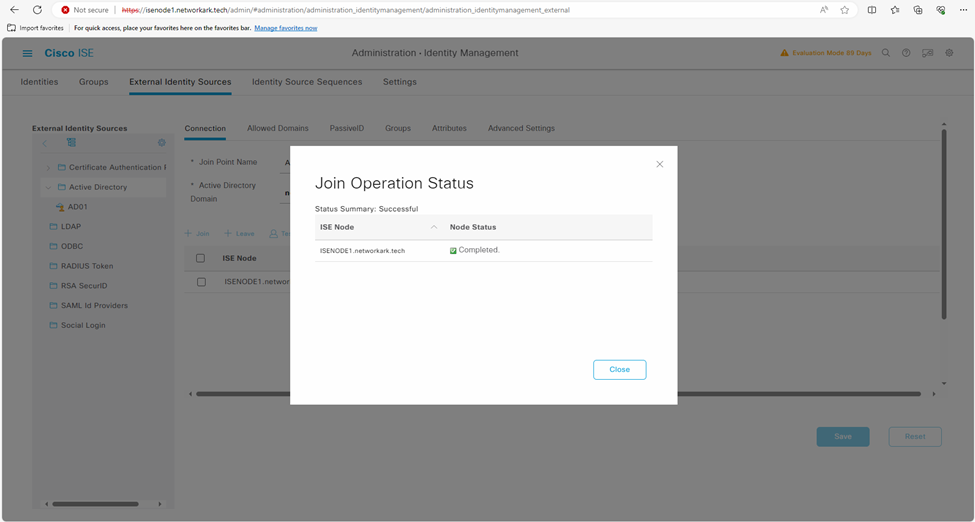
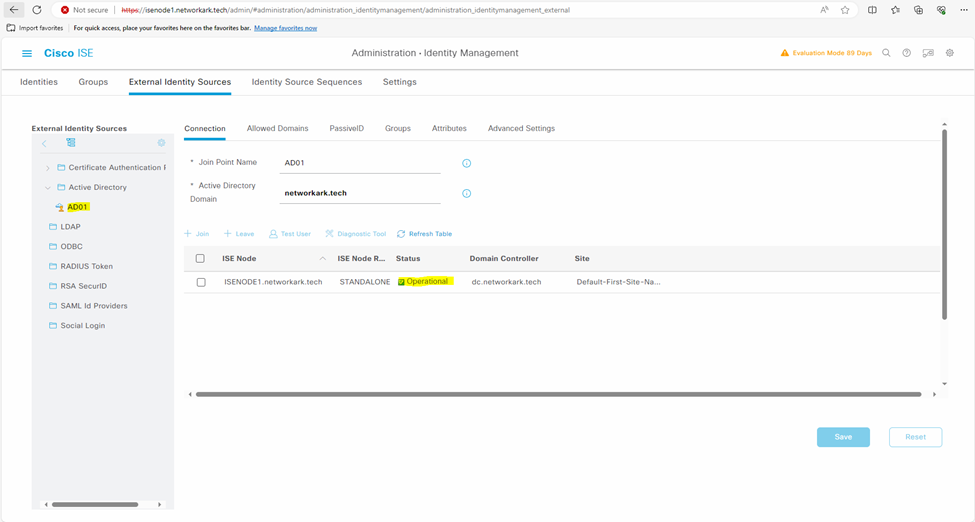
Step 2: Retrieve and Add Microsoft Active Directory Groups in Cisco ISE 3.2
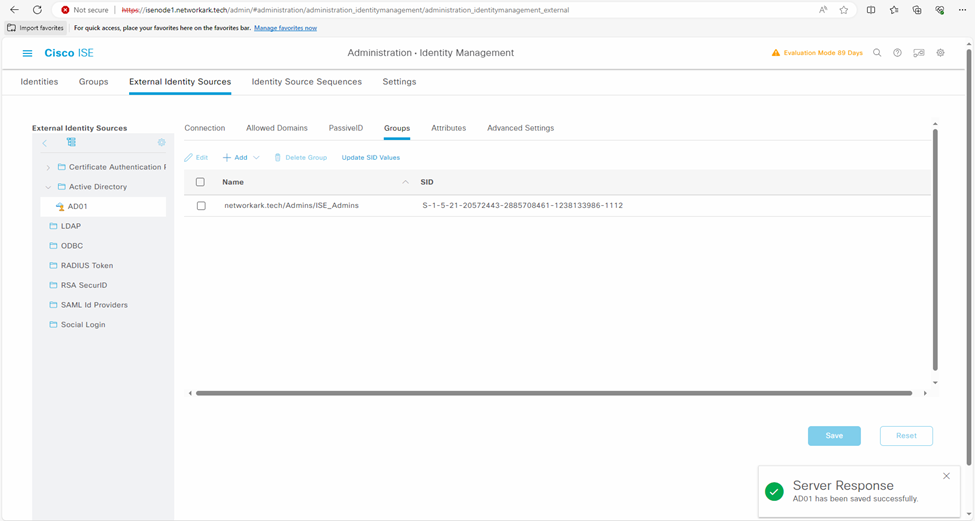
- Navigate to Administration -> Identity Management -> External Identity Sources -> Active Directory -> Groups -> Retrieve Groups.
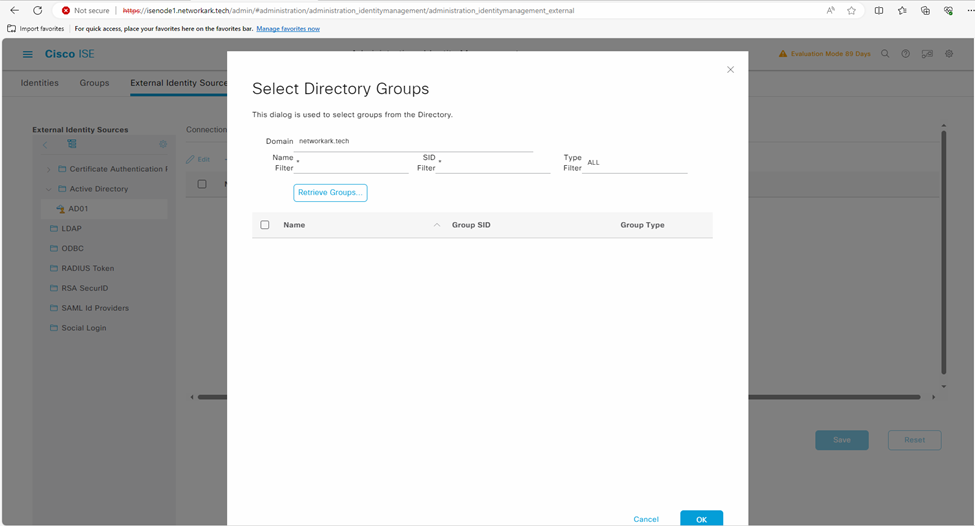
- Navigate to Administration -> Identity Management -> External Identity Sources -> Active Directory -> Groups -> Add -> Select groups form Directory such as “ISE_Admin” in this case.
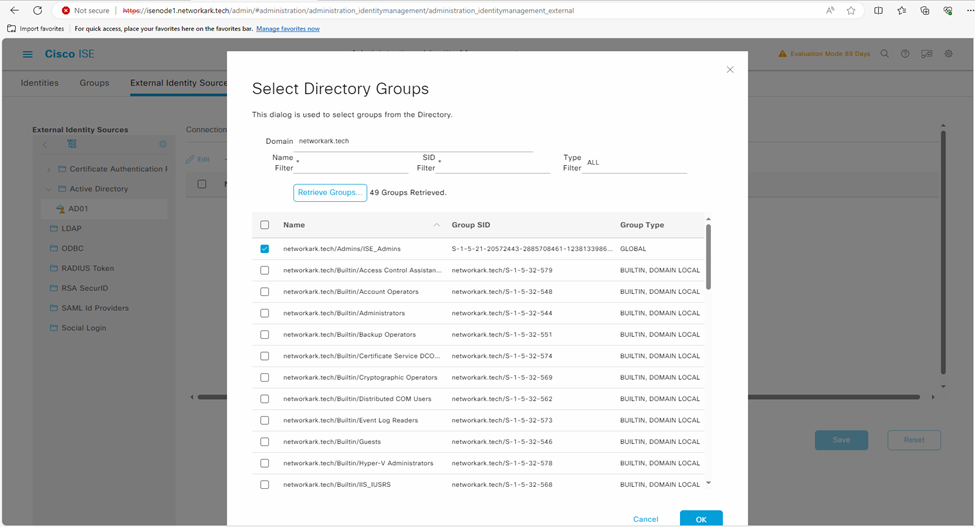
- Import at least one Microsoft Active Directory Group to which your admin accounts belong. You can add multiple groups as well.
Step 3: Enable Microsoft Active Directory for Administrative Access to Cisco ISE 3.2
- Navigate to Administration > System > Admin Access > Authentication.
- From the Authentication Method tab, choose the Password Based option and
- Choose Microsoft Active Directory profile created earlier from the Identity Source drop-down list.
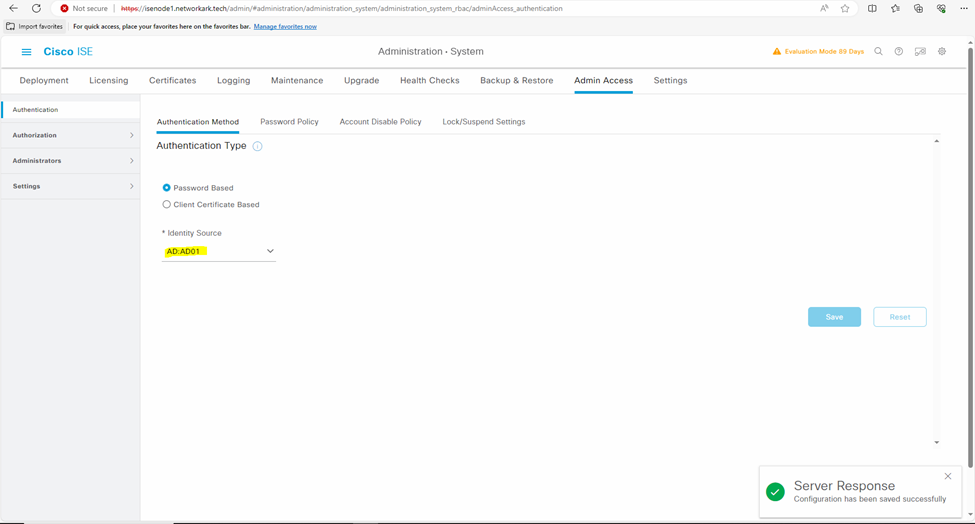
- Click Save Changes.
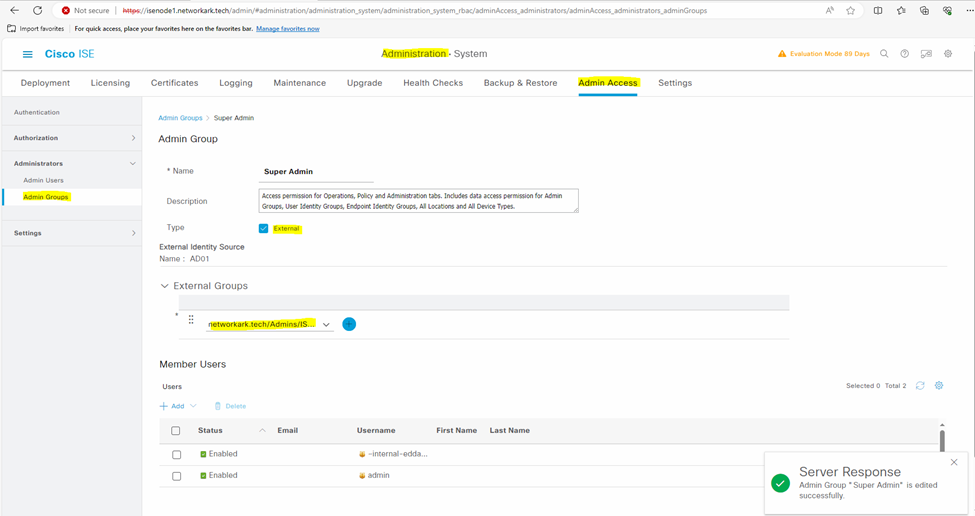
Step 4: Test and Verification
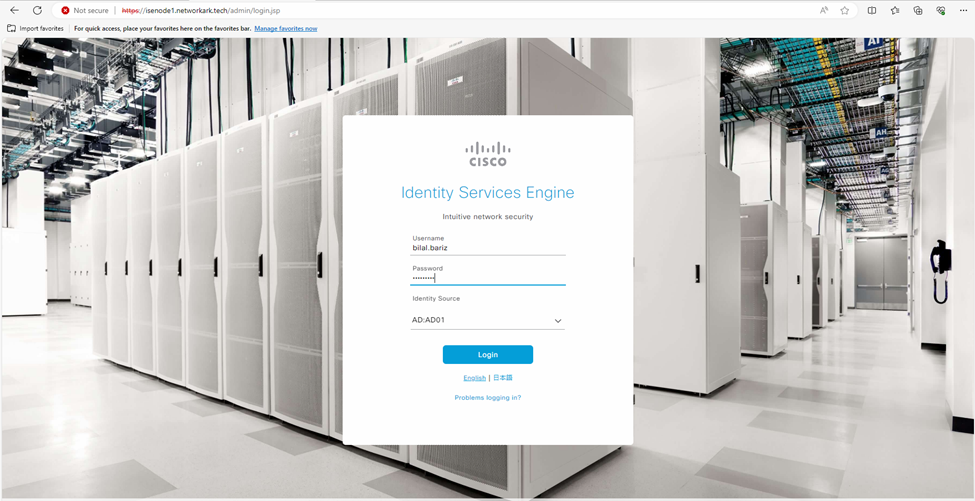
- Verficiation 1: Log out and login again using Microsoft Active Directory administrator account.
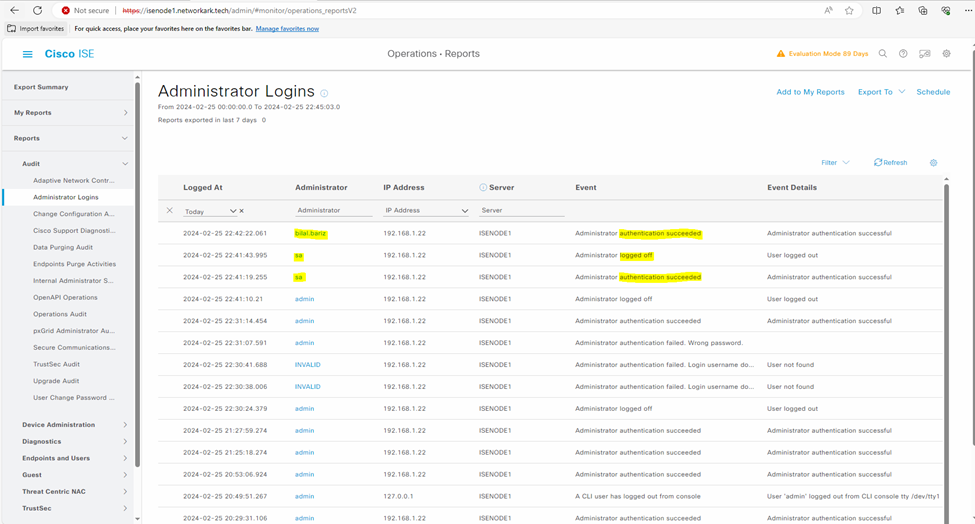
- Verficiation 2: Navigate to Operations > Reports > Audit > Administrator Logins
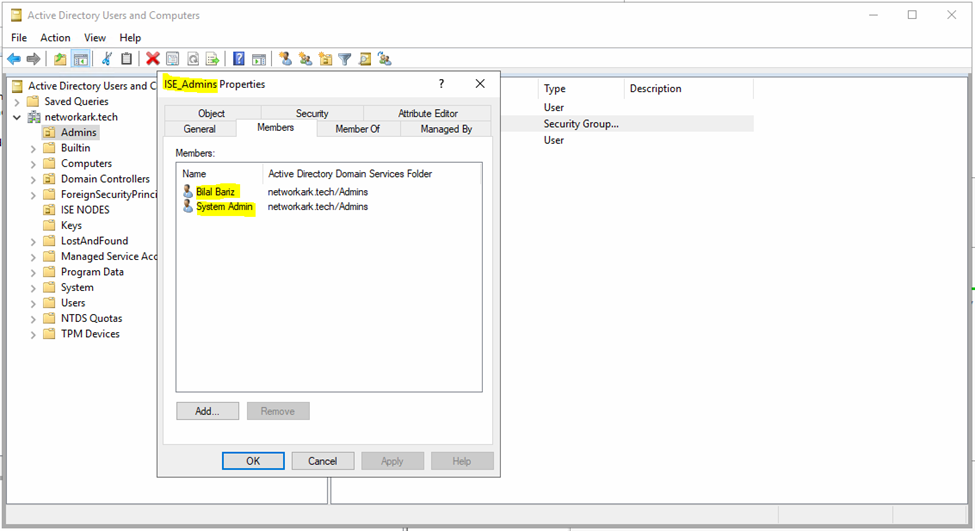
- Verficiation 3: We added Microsoft Active Directory group “ISE_Admins” in the Step 2:2 the group has two members where we used one of them “Bilal Bariz” to login to Cisco ISE 3.2 in the Step 3:1.
Regards,
Bilal Bariz
2xCCIE# 65780, PCNSE/C, PMP
Sr. Technical Architect – Network Security





